Logs
Activity Log
This feature is useful not only for standard report analysis but also for investigating immediate problems such as program failures, errors or suspicious activity. Firewall, Audit, Action, and Password includes many ready-to-use log display parameters. Press Enter and the specified data appears in seconds. You can also choose to print a hard copy of the Activity Log results. To use the Activity Log, follow this procedure.
The following example is based on Firewall but is relevant for all modules
- Navigate to Logs -> Firewall and click Firewall Log. A Filter screen is displayed.
- Select your parameters and click OK. The Log is displayed.
- Click Retrieve the next set of data to display the next 100 transactions.
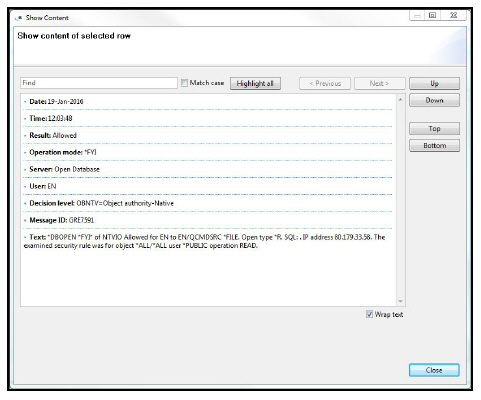
- Double-click a row to view the full log information.
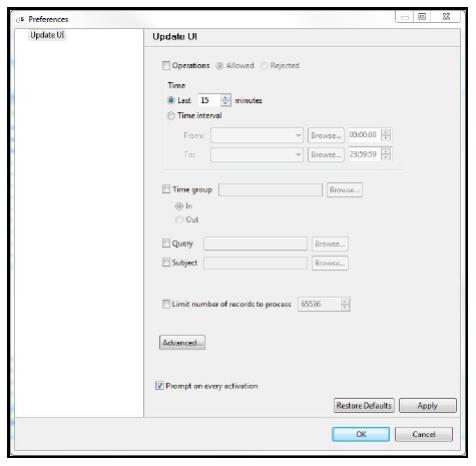
|
Options/Parameters |
Description |
|---|---|
|
Operations |
All = Show all log messages Reject = Show only reject messages Allow = Show only allow messages |
|
Time |
Display last n minutes = This Backward Glance feature lets you look at the last several minutes of activity without the need to define specific time or date parameters. Just enter how long a period (in minutes) you wish to look at, click Enter, and transactions occurring during that period of time quickly appear. Backward Glance really comes in handy when assisting users with those nasty error messages that pop up verifying that a batch job has successfully completed. Enter the desired number of minutes Display time interval = Selects only those events occurring within the range specified by the starting and ending date/time combination. |
|
Filter by time group |
The Activity Log displays make full use of the convenient time group feature. This time-saving feature further enhances your ability to reach your critical data quickly. Relationship: None = Do not use time group, even if included in query definition Out = Include all records not in time group (Exclusive) In = Include all records in time group (Inclusive) |
|
Query |
Use an existing query to filter Activity Log entries. This is useful for applying complex filter criteria. Name = Name of an existing query *None = Do not use query rules (Default) |
|
Maximum Numbers of Records |
*NOMAX = No maximum (Default) |
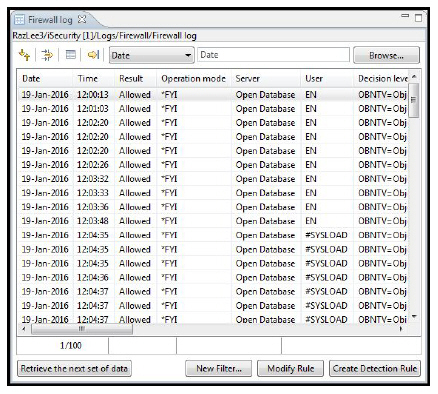
You can use Up, Down, Top, and Bottom to scroll within the log.
You can Select a log transaction and click Modify Rule to change a rule’s definitions. You can select a log transaction and click Create Detection Rule to add a new real time detection rule.
Export as CSV
This option allows you to save your Activity Logs in your computer in a CSV format. CSV Files (comma separated value files) are a standard format for transferring data between databases or spreadsheets (such as Microsoft Excel). CSV Files are ASCII encoded and so can be edited in any Text Editor.
To export Firewall logs to CSV format:
- Navigate to Logs -> Firewall and click Export as CSV. The Filter dialog is displayed.
- Set your parameters and click OK. Your PC opens a dialog where you can specify the directory to which to save the file and the name for the file.
- Navigate to the required directory, enter a name and click Save. Your log is now saved in CSV format.
Export Spreadsheet
This option allows you to save your Activity Logs in your computer in Excel, OpenOffice spreadsheet, HTML or PDF formats.
To export Firewall logs to a spreadsheet:
- Navigate to Logs -> Firewall and click Export. The Filter dialog is displayed.
- Choose your export format, set your parameters and click OK. Your PC opens a dialog where you can specify the directory to which to save the file and the name for the file.
- Navigate to the required directory, enter a name and click Save. Your log is now saved in a spreadsheet format.
